Secure FTP
In this guide, we will go through the process of installing a secure FTP server using OpenSSH on Rocky Linux 9.
SFTP (Secure File Transfer Protocol) is a secure file transfer protocol that uses SSH (Secure Shell) to provide encryption and authentication. Unlike FTP, SFTP uses a single connection to transfer files and provides a secure and encrypted channel for data communication.
Install OpenSSH
OpenSSH is the open-source implementation of the SSH protocol suite, which includes the SSH server and client applications. The minimal installation of Rocky Linux already contains it but if for whatever reason you need to install it, you can do so by running the following command:
sudo dnf install openssh-serverConfigure OpenSSH
After installation, the configuration file for OpenSSH can be found here: /etc/ssh/sshd_config.
Open the /etc/ssh/sshd_config file in your favourite text editor and comment on the existing Subsystem line, if present, and then add the following lines at the end of the file:
# override default of no subsystems
#Subsystem sftp /usr/libexec/openssh/sftp-server
Subsystem sftp internal-sftp
Match group sftpusers
ChrootDirectory %h
ForceCommand internal-sftp
X11Forwarding no
AllowTcpForwarding noHere, we have set the Subsystem to use the internal-sftp module for SFTP service. We have also set Match group sftpusers to limit SFTP access to only members of the sftpusers group. The ChrootDirectory %h directive sets the user’s home directory as the root directory. The ForceCommand internal-sftp directive forces the SFTP protocol to be used, and the X11Forwarding and AllowTcpForwarding directives are set to no to disable X11 and TCP forwarding.
Next, restart SSH and check the service status:
sudo systemctl restart sshd
systemctl status sshd
● sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2022-02-27 22:02:55 GMT
Docs: man:sshd(8)
man:sshd_config(5)
Main PID: 1331 (sshd)
Tasks: 1 (limit: 10655)
Memory: 4.1M
CPU: 320ms
CGroup: /system.slice/sshd.service
└─1331 "sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups"Create SFTP Group and Local User Accounts
Next, we need to create local user accounts for remote clients to access the SFTP server but first, let’s create the group we referenced in the /etc/ssh/sshd_config file sftpusers.
sudo groupadd sftpusersTo create a local user account called sftpuser, use the following command – this also adds the user to the group sftpusers:
sudo useradd -G sftpusers sftpuserNext, you can set a password for the user with the following command:
sudo passwd sftpuserConfigure Permissions
At this point, you can use SFTP and log in as sftpuser, but the user will not be restricted to the home directory only. To rectify that run the following commands:
sudo ls -ld /home/sftpuser/
drwx------. 2 sftpuser sftpuser 62 Feb 27 22:04 /home/sftpuser/
sudo chown root:sftpusers /home/sftpuser/
sudo chmod 755 /home/sftpusergd/
sudo ls -ld /home/sftpuser/
drwxr-xr-x. 2 root sftpusers 62 Feb 27 22:04 /home/sftpuser/You can see how the permissions were changed by the two commands in the middle – sftpuser has access only to their home directory now and if we try to access another directory like /home/ we will be greeted with “Failed to retrieve directory listing”. Also, we cannot SSH to the server using the sftp user account created either:
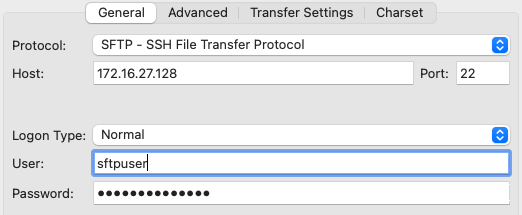
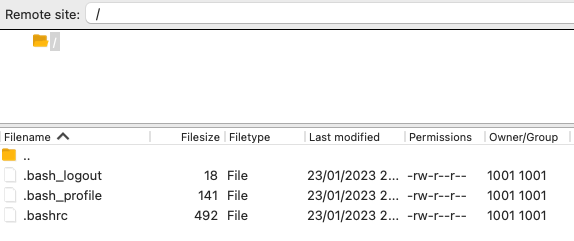
Status: Connecting to 172.16.27.128...
Status: Using username "sftpusergd".
Status: Connected to 172.16.27.128
Status: Retrieving directory listing...
Status: Directory listing of "/" successful
Status: Retrieving directory listing of "/home"...
Command: cd "/home"
Error: Directory /home: no such file or directory
Error: Failed to retrieve directory listing
ssh sftpuser@172.16.27.128
sftpusergd@172.16.27.128's password:
This service allows sftp connections only.
Connection to 172.16.27.128 closed.Congratulations, you have successfully deployed and configured a secure SFTP server using OpenSSH on Rocky Linux 9. The SFTP server only allows local user access. This configuration provides a secure and encrypted channel for data communication between the server and the remote clients.
